2020 Microsoft Hong Kong Top MSP Partner
8 April 2020
SCCM Deployment And Optimization
8 April 2024Conditional Access For Office 365 – What An Admin Needs To Know
Original article: https://www.enowsoftware.com/solutions-engine/conditional-access-for-office-365
“Azure Active Directory Conditional Access has been around since 2016. Conditional Access governs access to cloud resources by evaluating the conditions associated with the sign-in of a user or application accessing a resource. Conditional Access policies allow an admin to stipulate under what conditions certain actions are enabled. I like to think of them as If-then statements. For example: If: “Sign in comes from an untrusted network, accessing any cloud app”, then: “Require another form of authentication (MFA) before granting access to the cloud app”
A resource can be one of many SaaS applications integrated with Azure Active Directory (AAD) for instance 3rd Party applications such as Salesforce or Microsoft’s Exchange Online.
Up until recently, conditional access policies have had the granularity of allowing the administrator to create policies targeted for specific SaaS applications, such as Exchange Online or Microsoft Teams for example. Because of the deep integration and dependencies on other Office 365 services, restricting access to one application such as Teams for example will have inconsistent collaborative experiences. Some organizations prefer to have the same conditional access policy applied to many applications.
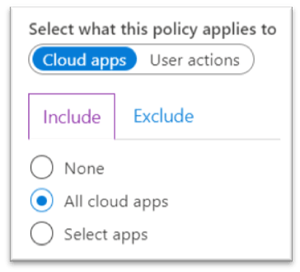
The restriction up until now has been it’s either ALL cloud apps you include in your policy, with the option to add exceptions, or individual cloud applications, and not a group of applications.
This allows for some room for error on the part of the administrator, in either configuring a policy incorrectly for one application or not catering for an application completely. There are approximately 32 Microsoft Cloud Applications and hundreds of Azure AD registered gallery applications.
Conditional Access for Office 365 (Preview)
Conditional Access for Office 365 (preview) was introduced on February 4th, 2020, and is already being rolled out to tenants. When I first heard about Conditional Access for Office 365 suite, my first thought was that it was a type of implementation of a conditional access administration experience in the Microsoft 365 admin center. Before you go looking on https://admin.microsoft.com for a “Conditional Access” workspace, I’ll save you the trouble, it’s not. If you have experience creating conditional access policies in the Azure Active Directory portal (https://portal.azure.com), the admin experience is the same.
Licensing
Conditional Access for Office 365 suite requires AAD Premium P1 or AAD Premium P2 and is not available to AAD Free or AAD Office 365 apps. This can be misleading as some people may have been led to believe that the new Conditional Access for Office 365 (preview) feature would be available to non-premium versions of Azure Active Directory.
To expand a little on the licensing requirements for Conditional Access to Office 365 suite, I will attempt to explain the flavors of Azure Active Directory (AAD). There are four flavors of AAD, namely:
- Free – which comes with any Microsoft SaaS app such as PowerBI, Azure, Dynamics 365, etc. There is no Conditional Access included in Free.
- Office 365 apps – which are included with Office 365 E1, E3, E5, and F1 subscriptions. This version of AAD does not include Conditional Access.
- Premium P1 – can be purchased as an additional license per user. This version includes Conditional Access. Premium P1 is also included as part of Enterprise Mobility and Security (EM+S) E3 and Microsoft 365 E3.
- Premium P2 – can be purchased as an additional license per user. This version includes Conditional Access as well as risk-based Conditional Access and Privileged Identity Management (PIM). Premium P2 is also included as part of Enterprise Mobility and Security (EM+S) E5 and Microsoft 365 E5.
Microsoft 365 Business includes a subset of AAD Premium P1 which does include Conditional Access.
Conditional Access for Office 365 suite is merely an enhancement to the configuration options available in Conditional Access, so license requirements will be that of Conditional Access.
Admin’s Guide to Conditional Access for Office 365
Conditional Access for the Office 365 suite gives admins the ability to assign a single conditional access policy across the Office 365 suite of services and apps with one click, or one umbrella app as I like to call it.

Conditional Access for the Office 365 suite gives admins the ability to assign a single conditional access policy across the Office 365 suite of services and apps with one click, or one umbrella app as I like to call it.
This provides consistent coverage by setting a single policy across Office 365 apps.
Office 365 (Preview) is a group of applications related to one another and part of the Office 365 suite of applications. Office 365 (preview) is listed as one single app in the conditional access “cloud apps or applications” selection blade in the assignments section of a Conditional Access policy. The “single” app allows administrators of conditional access policies to target the following services all at once:
- Microsoft Flow
- Microsoft Forms
- Microsoft Stream
- Microsoft Teams
- Microsoft To-Do
- Office 365 Exchange Online
- Office 365 Search Service
- Office 365 SharePoint Online
- Office 365 Yammer
- Office Delve
- Office Online
- COM
- OneDrive
- PowerApps
- Skype for Business Online
- Sway
So now, instead of targeting individual cloud apps and potentially facing issues related to inconsistent policies and dependencies, Microsoft recommends targeting this group of applications in one policy. Administrators can, of course, choose to exclude specific apps from the policy if they wish by including “Office 365 (preview)” (under the “Include” tab of cloud apps and actions blade) and then excluding the specific apps of their choice (under the “exclude” tab of the cloud apps and actions blade).
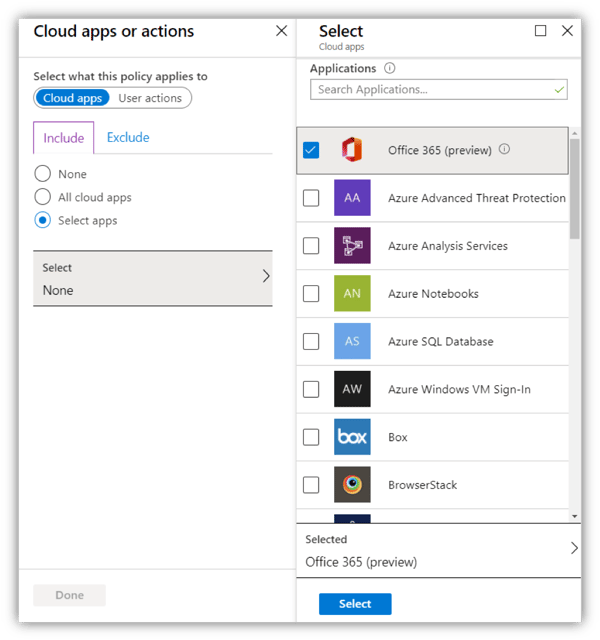
In the screenshot above, Cloud apps selection blade in Conditional Access policy, one can see the new “Office 365 (preview)” app is listed first, this is intentional so that it is easy for admins to find.
As previously mentioned, admins who might be creating Conditional Access policies with the same controls and actions for each of the individual Office 365 suite applications, can now consolidate these policies into one without inconsistencies and better integration experiences for their end-users. This minimizes the number of Conditional Access policies admins need to create and maintain going forward.
I recently presented a session at Microsoft Ignite: The Tour where I spoke about Conditional Access in the real world. I provided some examples of how granular one can get with Conditional Access policies and not just block access. When multiple Conditional Access policies apply to a user accessing a cloud app, all of the policies must grant access before the user can access the cloud app or resource. This doesn’t mean that users are blocked by default as some admins think is the case. If one policy blocks access, a block action trumps all other configurations, and the user will be blocked and not required to satisfy any other controls.
In conclusion, if you have been applying conditional access policies to individual Office 365 apps, try out the new Office 365 suite (preview) app and create a policy in the “Report-only” mode to evaluate the impact of the new configuration without impacting your users.”